Modern Geo location Variations are classified based on three
Hill Station view :
- Triangulation
- Trilateration
- Multiateration
Triangulation:
Triangulation is actually just an average of latitudes and longitudes gathered using the signal strength squared as the weight is called as weighted centroid Trilateration.
Triangulation assume the signal strength will change at the inverse square of the distance.
Triangulation is the process of determining the location of a point by measuring angles to it from known points at either end of a fixed line.
You can check how to triangulate using above link.
Trilateration:
Trilateration is the process of determining absolute location of points by measurement of distances using the geometry of circle, spheres or triangles.
To check Trilateration check the below link
Ekahau Software:
Software used for site survey planning, mobile surveys, spectrum analyser and heat mapper.
Accuware:
Accuware used to WiFi location monitor. No mobile application required for the target.
Multiateration:
Multilateration is a navigation and surveillance technique based on the measurement of the times of arrival of energy waves having a known propagation speed. Multilateration is used by military forces to find the exact geo location of target based on the time difference.
https://valparaihillsheaven.blogspot.com/2019/?m=1
How to secure devices from cyber threats:
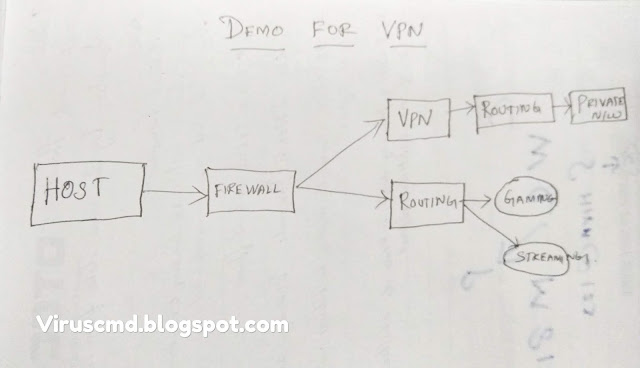
Https://viruscmd.blogspot.com
How to secure devices from cyber threats:
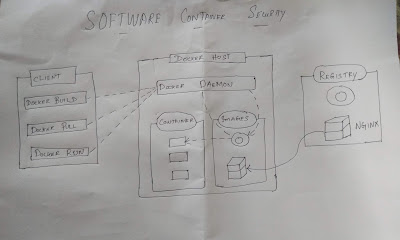
Https://viruscmd.blogspot.com